picoCTF Forensics
August 22, 2022

SPOILER ALERT : This is a writeup for the picoCTF Forensics. It will show you how to solve the problem; There may not be all of them. But I’ll keep updating every day and may not have complete details, But if you want a way to do it, I have it for you.
If you want to play picoCTF click here
[1] information
Description : Files can always be changed in a secret way. Can you find the flag? cat.jpg
You can use this command to verify that this file is actually jpg file
file [file_name]
it’s actually .jpg file then you can use Exiftool to see details about this file
exiftool cat.jpg
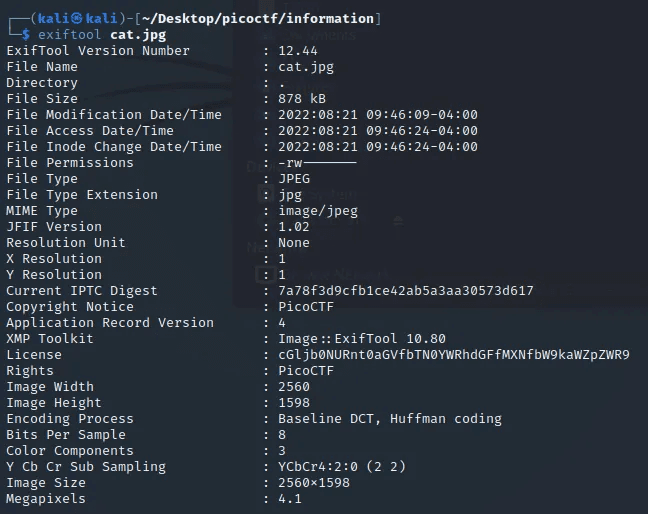
There’s something really interesting in the License section, where this strings set might be the answer we’re looking for. and the faster way to decode strings is
echo cGljb0NURnt0aGVfbTN0YWRhdGFfMXNfbW9kaWZpZWR9 | base64 -d
[2] Matryoshka doll
Description : Matryoshka dolls are a set of wooden dolls of decreasing size placed one inside another. What’s the final one? Image : this
Hint : Wait, you can hide files inside files? But how do you find them?
The Command that you can see the hidden file is Binwalk
binwalk -e dolls.jpg
# -e is extract
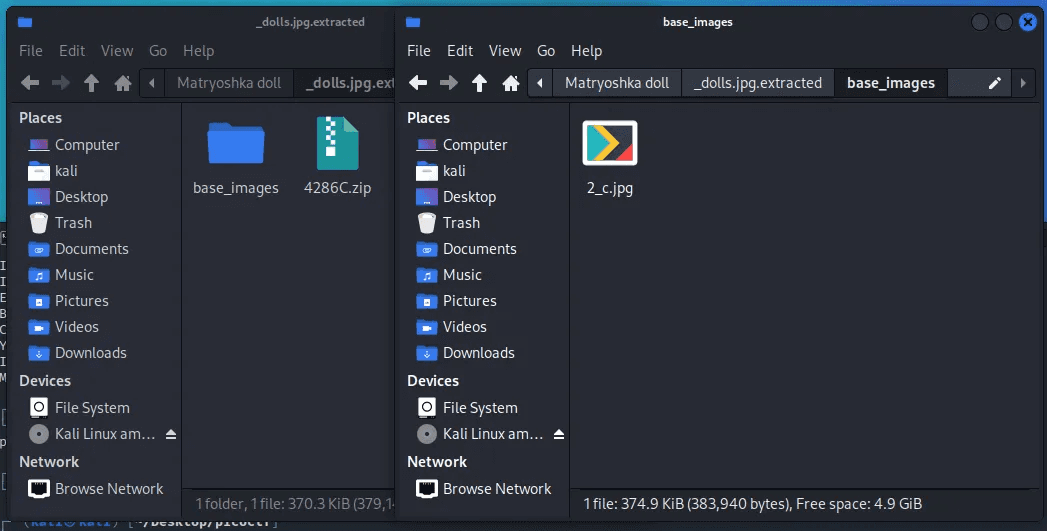
After extracting the file, You will see the base_images folder. In this folder, there is one image that you will need to use the same command to extract file
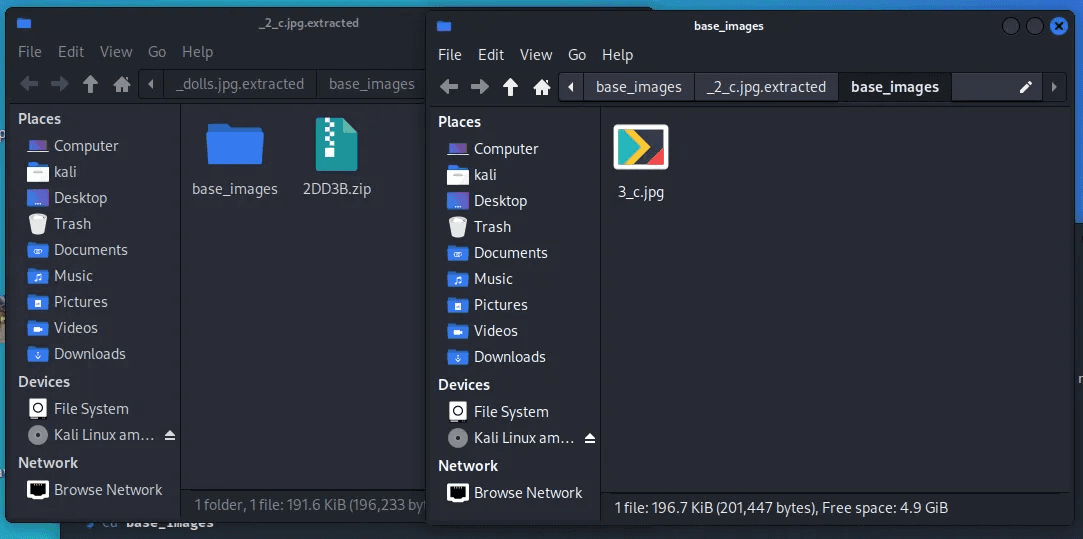
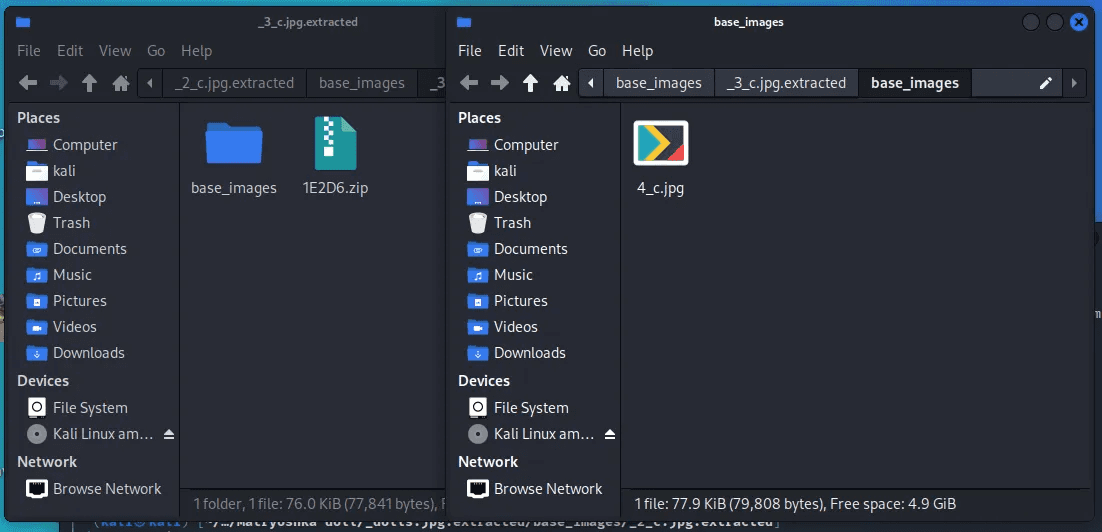
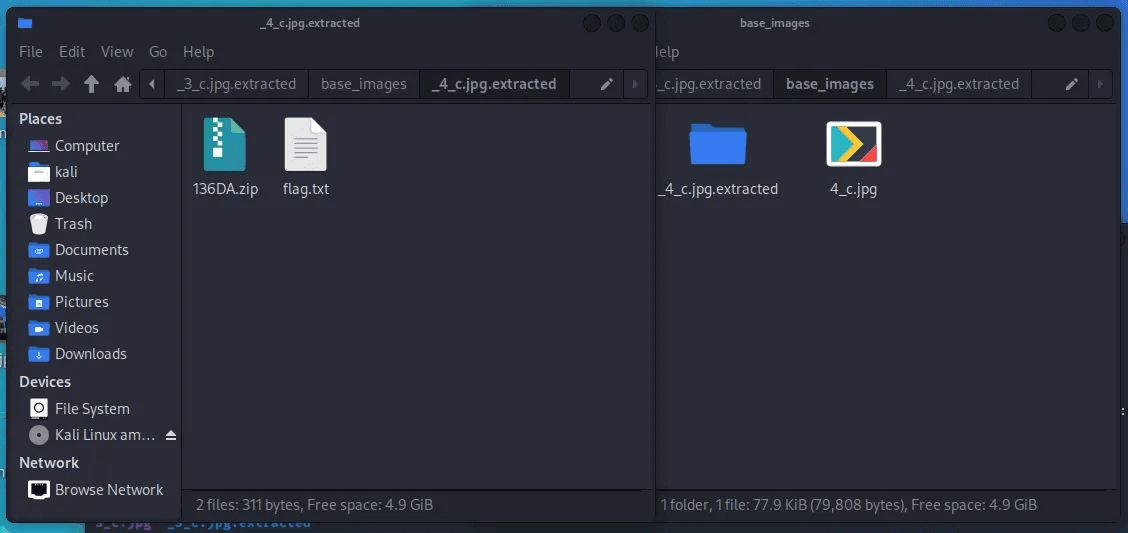
As you can see in the 4th round of the binwalk command, we’ve got the flag file. You’ll find the flag you were looking for when you open it. But you have to delete the strings you don’t want. You will get the perfect flag.
[3] Glory of the Garden
Description : This garden contains more than it seems.
Hint : What is a hex editor?
When you open the file it looks like nothing is wrong. it’s a general image So let’s try the Binwalk command to see if it has hidden file.
binwalk garden.jpg
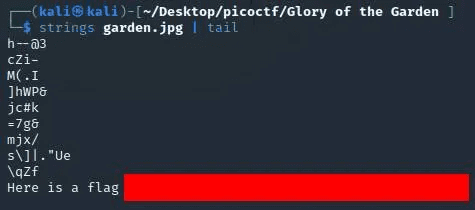
ok, something look interesting in output let’s try Strings command to print the strings of printable characters in files
strings garden.jpg | tail
[4] Wireshark doo dooo do doo…
Description : Can you find the flag? shark1.pcapng.
Hint : (none)
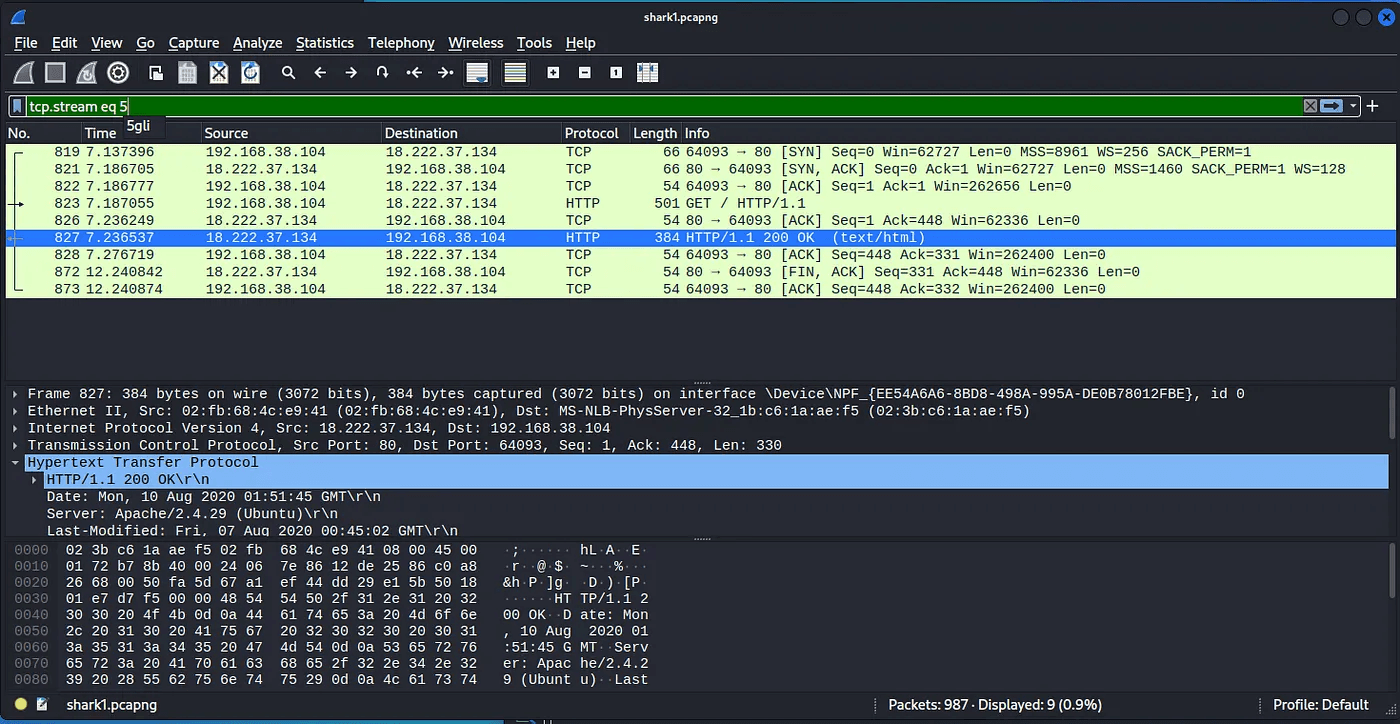
You’ll need Wireshark to view or transfer files over the network, but if you’re using Kali Linux, you can open files without additional loading. after you open shark1.pcapng you’ll need you filter with this
tcp.stream eq 5
You’ll see the info that show (text/html) in HTTP protocal.
After that, right-click and press follow → HTTP stream to view information. And you’ll see a message that appears to be the answer. But not because you have to decode it.
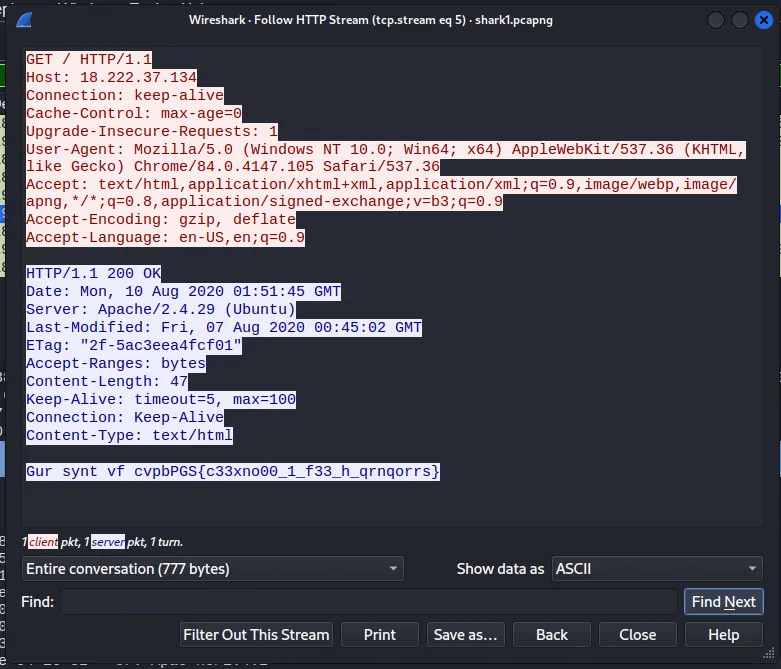
You can decode it in this site with ROT13 and you’ll get the right flag